czezz
October 22, 2020, 3:26pm
1
Hi all,
And I puzzled what command “kubectl expose” actually does:kubectl expose deployment hello-node --type=LoadBalancer --port=8080
I assume it exposes/shares service running on port 8080 inside pod/container hello-node.
user1@user:~$ kubectl get service
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
hello-node LoadBalancer 10.99.96.18 <pending> 8080:30397/TCP 84m
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 4d2h
However, I do NOT see any service LISTENING on port 8080 inside of hello-node containerdocker exec -it 74d84fd550c8 ss -ln | grep 8080
Question: why this tutorial asks me to expose service on port 8080 when there is no such service on the pod/container?
The ss command is not available in that container.
root@924faddaa888:~# ss
bash: ss: command not found
Here is the output if I exec in and curl port 8080:
root@924faddaa888:/# curl 127.0.0.1:8080
CLIENT VALUES:
client_address=127.0.0.1
command=GET
real path=/
query=nil
request_version=1.1
request_uri=http://127.0.0.1:8080/
SERVER VALUES:
server_version=nginx: 1.10.0 - lua: 10001
HEADERS RECEIVED:
accept=*/*
host=127.0.0.1:8080
user-agent=curl/7.47.0
BODY:
-no body in request-
Also the nginx config inside the container shows port 8080:
root@924faddaa888:/etc/nginx# cat /etc/nginx/nginx.conf | grep 8080
listen 8080 default_server reuseport;
Kind regards,
czezz
October 23, 2020, 8:22am
3
Hi Stephen,
user1@user:~$ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
74d84fd550c8 gcr.io/k8s-minikube/kicbase:v0.0.13 "/usr/local/bin/entr…" 4 days ago Up 45 hours 127.0.0.1:32771->22/tcp, 127.0.0.1:32770->2376/tcp, 127.0.0.1:32769->5000/tcp, 127.0.0.1:32768->8443/tcp minikube
user1@user:~$ docker exec -it 74d84fd550c8 /bin/bash
root@minikube:/# which ss
/usr/bin/ss
root@minikube:/# curl 127.0.0.1:8080
curl: (7) Failed to connect to 127.0.0.1 port 8080: Connection refused
root@minikube:/# curl 127.0.0.1:8080
curl: (7) Failed to connect to 127.0.0.1 port 8080: Connection refused
root@minikube:/# cat /etc/nginx/nginx.conf | grep 8080
cat: /etc/nginx/nginx.conf: No such file or directory
Hi @czezz ,
You are docker execing in to the Minikube container, not the echoserver pod.
Instead, try running kubectl get podskubectl exec in to the echoserver pod.
Kind regards,
czezz
October 23, 2020, 3:02pm
5
Hi Stephen,
Questions:
I assume hello-node POD/Deployment contains inside docker container: 74d84fd550c8 - correct?
If so, where is actually nginx installed?
user1@user:~$ docker exec -it 74d84fd550c8 /bin/bash
whereas, inside POD/Deployment I see nginx files, SOCKET on port 8080 and cant really display “ps”:
user1@user:~$ kubectl exec hello-node-7567d9fdc9-qjgvk – find / -type f -iname “nginx ”
Does that mean nginx is partly installed on hello-node POD/Deployment and partly on Docker?
Hey, @czezz
Pod is not running your application container, it’s just giving the environment to that apps container. Environment could be anything, In respect of namespace, network, volume etc.
Did you check the nginx.conf file ?
czezz
October 23, 2020, 3:19pm
7
Hi @tej-singh-rana ,@stephendotcarter has already mentioned and I confirmed that. I am not asking for that.
czezz
October 23, 2020, 3:26pm
9
Thanks @tej-singh-rana , already read it before.
I post here my questions again:
where is actually nginx installed?
user1@user:~$ docker exec -it 74d84fd550c8 /bin/bash
whereas, inside POD/Deployment I see nginx files, SOCKET on port 8080 and cant really display “ps”:
user1@user:~$ kubectl exec hello-node-7567d9fdc9-qjgvk – find / -type f -iname “nginx”
/usr/sbin/nginx
/run/nginx.pid
/etc/nginx/nginx.conf.default
/etc/nginx/nginx.conf
Does that mean nginx is partly installed on hello-node POD/Deployment and partly on Docker?
czezz
October 23, 2020, 6:48pm
10
The more I read the the less I understand.
Question:
user1@user:~$ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
74d84fd550c8 gcr.io/k8s-minikube/kicbase:v0.0.13 "/usr/local/bin/entr…" 5 days ago Up 2 days 127.0.0.1:32771->22/tcp, 127.0.0.1:32770->2376/tcp, 127.0.0.1:32769->5000/tcp, 127.0.0.1:32768->8443/tcp minikube
user1@user:~$ docker exec 74d84fd550c8 cat /etc/hostname
minikube
user1@user:~$ docker exec 74d84fd550c8 which nginx
{this means there is no nginx binary/package}
user1@user:~$ kubectl get po
NAME READY STATUS RESTARTS AGE
hello-node-7567d9fdc9-qjgvk 1/1 Running 0 35h
user1@user:~$ kubectl exec hello-node-7567d9fdc9-qjgvk -- cat /etc/hostname
hello-node-7567d9fdc9-qjgvk
user1@user:~$ kubectl exec hello-node-7567d9fdc9-qjgvk -- which nginx
/usr/sbin/nginx <--- {this means nginx is here}
The container running nginx is running inside the minikube docker container.
Try this, docker exec in to the minikube container.
Then:
lsns | grep nginx
The using the 4th number which is the PID:
nsenter -t 6831 --net ss -lpn | grep 8080
You have to keep in mind that because you are running minikube, your entire Kubernetes cluster is running inside a container which make everything slightly more complicated to get your head around.
docker ps
Kind regards,
czezz
October 26, 2020, 7:30pm
12
Hi Stephen,
By digging deeper of what you showed with nsenter, I tried this:
user1@user:~$ docker exec -it 74d84fd550c8 /bin/bash
root@minikube:~# nsenter -t 2437 -m
-bash: mesg: command not found
*{now I am in the namespace}*
# ls -al /etc/nginx/nginx.conf
-rw-r----- 1 root root 2119 May 28 2016 /etc/nginx/nginx.conf
It looks like this is what I see inside of the POD:
user1@user:~$ kubectl exec hello-node-7567d9fdc9-qjgvk – find / -type f -iname “nginx”
/usr/sbin/nginx
/run/nginx.pid
/etc/nginx/nginx.conf.default
/etc/nginx/nginx.conf <--- HERE
Question:
–
Yes thats accurate, but again, keep in mind that you are trying to understand minikube, which is a kind of “nested” Kubernetes in a container.
Usually with Kubernetes the processes running inside docker container 74d84fd550c8 would be spread across multiple control plane and worker VM. Kubernetes just runs your pod as one or more Docker containers on a worker VM.
My suggestion is don’t get too obsessed with the low level details as some are minikube specific. Understanding the higher level constructs of Kubernetes is far more beneficial.
Kind regards,
czezz
October 27, 2020, 4:31pm
14
Hi Stephen,
In other words Kubernetes creates Namespace for nginx processes inside of Docker container.
If so, sentence under following link: Pods | Kubernetes
I would put it that way: “you can think of Pod as a wrapper around container’s dedicated namespace”
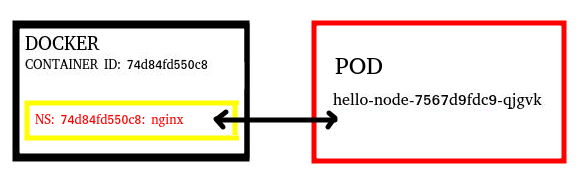
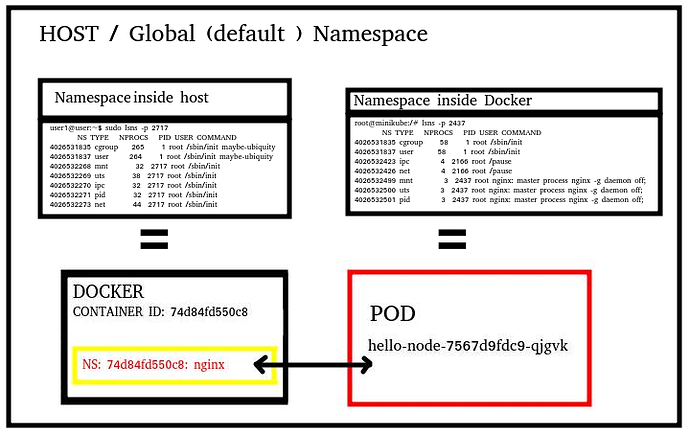
Here is full picture of my understanding (so far)
And here is a few more exercises I did today to better understand what is happening under the hood:
root@user:/home/user1# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
74d84fd550c8 gcr.io/k8s-minikube/kicbase:v0.0.13 "/usr/local/bin/entr…" 9 days ago Up 21 hours 127.0.0.1:32771->22/tcp, 127.0.0.1:32770->2376/tcp, 127.0.0.1:32769->5000/tcp, 127.0.0.1:32768->8443/tcp minikube
user1@user:~$ docker inspect 74d84fd550c8 | grep -i pid
"Pid": 2717,
"PidMode": "",
"PidsLimit": null,
user1@user:~$ sudo lsns -p 2717
NS TYPE NPROCS PID USER COMMAND
4026531835 cgroup 268 1 root /sbin/init maybe-ubiquity
4026531837 user 267 1 root /sbin/init maybe-ubiquity
4026532268 mnt 32 2717 root /sbin/init
4026532269 uts 38 2717 root /sbin/init
4026532270 ipc 32 2717 root /sbin/init
4026532271 pid 32 2717 root /sbin/init
4026532273 net 44 2717 root /sbin/init
user1@user:~$ sudo nsenter -m -u -p -n -i -t 2717 bash
root@minikube:/# <-- im in docker container: 74d84fd550c8 == docker exec -it 74d84fd550c8 /bin/bash
root@minikube:/# lsns -p 2437
NS TYPE NPROCS PID USER COMMAND
4026531835 cgroup 58 1 root /sbin/init
4026531837 user 58 1 root /sbin/init
4026532423 ipc 4 2166 root /pause
4026532426 net 4 2166 root /pause
4026532499 mnt 3 2437 root nginx: master process nginx -g daemon off;
4026532500 uts 3 2437 root nginx: master process nginx -g daemon off;
4026532501 pid 3 2437 root nginx: master process nginx -g daemon off;
root@minikube:/# sudo nsenter -m -u -p -n -i -t 2437 bash
root@hello-node-7567d9fdc9-qjgvk:/# <-- im in nginx namespace stands for hello-node-7567d9fdc9-qjgvk pod == kubectl exec -ti hello-node-7567d9fdc9-qjgvk -- /bin/bash
user1@user:~$ ps auxf -ww
...
root 739 0.0 1.2 969252 26384 ? Ssl 05:25 0:17 /usr/bin/containerd
root 2693 0.0 0.1 110128 3428 ? Sl 05:33 0:00 \_ containerd-shim -namespace moby -workdir /var/lib/containerd/io.containerd.runtime.v1.linux/moby/74d84fd550c8b008bcd0ce3d92f764942a310bdcb9b3a25199e7241e92a6078d -address /run/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 2717 0.0 0.2 169284 4088 ? Ss 05:33 0:00 \_ /sbin/init
root 2924 0.0 0.2 29240 4232 ? S<s 05:33 0:00 \_ /lib/systemd/systemd-journald
root 2935 0.0 0.0 5568 760 ? Ss 05:33 0:00 \_ /usr/sbin/cron -f
_apt 2938 0.0 0.0 224092 504 ? Ssl 05:33 0:00 \_ /usr/sbin/rsyslogd -n -iNONE
root 2944 0.0 1.0 896420 20412 ? Ssl 05:33 0:16 \_ /usr/bin/containerd
root 2955 1.2 2.8 1344932 57716 ? Ssl 05:33 7:34 \_ /usr/bin/dockerd -H tcp://0.0.0.0:2376 -H unix:///var/run/docker.sock --default-ulimit=nofile=1048576:1048576 --tlsverify --tlscacert /etc/docker/ca.pem --tlscert /etc/docker/server.pem --tlskey /etc/docker/server-key.pem --label provider=docker --insecure-registry 10.96.0.0/12
root 2987 0.1 1.1 1404412 23508 ? Ssl 05:33 0:46 | \_ containerd --config /var/run/docker/containerd/containerd.toml --log-level info
root 4346 0.0 0.0 108700 540 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/d1f5928a50227ff021bba2e50621139f90563e853e1d01db383b1e672df45048 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 4419 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 4347 0.0 0.0 110108 772 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/723398c6fe35cc22357db12f7ca8c7add7b06a22c4f3a200430d10d4697f6b12 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 4405 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 4348 0.0 0.0 110108 508 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/9d45aee0944c4d35b263ee81f6f06fd234cced5be7e238c239928162db8e223e -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 4426 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 4465 0.0 0.0 108700 616 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/60bf4ef2010fb5a59a9cd398f9904554c5a35276f7c84e202035518332b0b619 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 4520 3.6 13.0 1096456 265740 ? Ssl 05:33 21:53 | | \_ kube-apiserver --advertise-address=192.168.49.2 --allow-privileged=true --authorization-mode=Node,RBAC --client-ca-file=/var/lib/minikube/certs/ca.crt --enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,DefaultStorageClass,DefaultTolerationSeconds,NodeRestriction,MutatingAdmissionWebhook,ValidatingAdmissionWebhook,ResourceQuota --enable-bootstrap-token-auth=true --etcd-cafile=/var/lib/minikube/certs/etcd/ca.crt --etcd-certfile=/var/lib/minikube/certs/apiserver-etcd-client.crt --etcd-keyfile=/var/lib/minikube/certs/apiserver-etcd-client.key --etcd-servers=https://127.0.0.1:2379 --insecure-port=0 --kubelet-client-certificate=/var/lib/minikube/certs/apiserver-kubelet-client.crt --kubelet-client-key=/var/lib/minikube/certs/apiserver-kubelet-client.key --kubelet-preferred-address-types=InternalIP,ExternalIP,Hostname --proxy-client-cert-file=/var/lib/minikube/certs/front-proxy-client.crt --proxy-client-key-file=/var/lib/minikube/certs/front-proxy-client.key --requestheader-allowed-names=front-proxy-client --requestheader-client-ca-file=/var/lib/minikube/certs/front-proxy-ca.crt --requestheader-extra-headers-prefix=X-Remote-Extra- --requestheader-group-headers=X-Remote-Group --requestheader-username-headers=X-Remote-User --secure-port=8443 --service-account-key-file=/var/lib/minikube/certs/sa.pub --service-cluster-ip-range=10.96.0.0/12 --tls-cert-file=/var/lib/minikube/certs/apiserver.crt --tls-private-key-file=/var/lib/minikube/certs/apiserver.key
root 4482 0.0 0.0 110108 564 ? Sl 05:33 0:01 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/f9ff3d2aa5af12ccec1178847c4001070fef8819c0184890ea23dd275d52afa4 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 4534 0.9 2.9 10612724 59068 ? Ssl 05:33 5:41 | | \_ etcd --advertise-client-urls=https://192.168.49.2:2379 --cert-file=/var/lib/minikube/certs/etcd/server.crt --client-cert-auth=true --data-dir=/var/lib/minikube/etcd --initial-advertise-peer-urls=https://192.168.49.2:2380 --initial-cluster=minikube=https://192.168.49.2:2380 --key-file=/var/lib/minikube/certs/etcd/server.key --listen-client-urls=https://127.0.0.1:2379,https://192.168.49.2:2379 --listen-metrics-urls=http://127.0.0.1:2381 --listen-peer-urls=https://192.168.49.2:2380 --name=minikube --peer-cert-file=/var/lib/minikube/certs/etcd/peer.crt --peer-client-cert-auth=true --peer-key-file=/var/lib/minikube/certs/etcd/peer.key --peer-trusted-ca-file=/var/lib/minikube/certs/etcd/ca.crt --proxy-refresh-interval=70000 --snapshot-count=10000 --trusted-ca-file=/var/lib/minikube/certs/etcd/ca.crt
root 4483 0.0 0.0 108700 756 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/41eeda21f67cabdeacc9ae4ad34a429144e75c687b90f3cc4b50d7409e4db200 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 4526 1.1 2.3 811368 47736 ? Ssl 05:33 6:49 | | \_ kube-controller-manager --authentication-kubeconfig=/etc/kubernetes/controller-manager.conf --authorization-kubeconfig=/etc/kubernetes/controller-manager.conf --bind-address=127.0.0.1 --client-ca-file=/var/lib/minikube/certs/ca.crt --cluster-name=mk --cluster-signing-cert-file=/var/lib/minikube/certs/ca.crt --cluster-signing-key-file=/var/lib/minikube/certs/ca.key --controllers=*,bootstrapsigner,tokencleaner --kubeconfig=/etc/kubernetes/controller-manager.conf --leader-elect=false --port=0 --requestheader-client-ca-file=/var/lib/minikube/certs/front-proxy-ca.crt --root-ca-file=/var/lib/minikube/certs/ca.crt --service-account-private-key-file=/var/lib/minikube/certs/sa.key --use-service-account-credentials=true
root 4680 0.0 0.0 108700 596 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/46ac8114ff14d7b78c2ae07a6e58182866b8d0ca8119d1504b604e7c38a96ed7 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 4724 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 4735 0.0 0.0 108700 740 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/36af84a1bf148b24620952d0af1c9e5431dabe0f52d0133d76aa532244d1b9ea -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 4751 0.1 0.8 746652 17972 ? Ssl 05:33 1:00 | | \_ kube-scheduler --authentication-kubeconfig=/etc/kubernetes/scheduler.conf --authorization-kubeconfig=/etc/kubernetes/scheduler.conf --bind-address=127.0.0.1 --kubeconfig=/etc/kubernetes/scheduler.conf --leader-elect=false --port=0
root 5011 0.0 0.0 108700 776 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/0c4911a2b46f87ee4c216e35c6d12c1025f9963420fb36166a1e52452251c6f9 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5033 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 5056 0.0 0.0 108700 596 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/d4022f2bb2884b4716dd50102149315bcc7c41fc2be7a1d8e3fbea94d6d8be24 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5104 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 5062 0.0 0.0 108700 728 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/d12665ab45df1b305c7957e5d2a0ec876c4c5b7d51636fb9af9a9697824d3c7b -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5099 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 5130 0.0 0.0 110108 600 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/506698be21ec585bfe6c7572eba227d620f61bdc996c08cc0eebf5b898336949 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5192 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 5220 0.0 0.0 110108 816 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/a1187ccfa9bd45212314367cbc82c9884ebaf3dffdf998efe027a49826d23670 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
nobody 5242 0.0 0.3 743156 6528 ? SLsl 05:33 0:05 | | \_ /tiller
root 5249 0.0 0.0 110108 616 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/fad5e4cdadf58994a78fa98ccfe50d8b7ff15020ac9e45779d67ff0166068687 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5300 0.0 0.7 743408 14948 ? Ssl 05:33 0:04 | | \_ /usr/local/bin/kube-proxy --config=/var/lib/kube-proxy/config.conf --hostname-override=minikube
root 5380 0.0 0.0 108700 616 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/7fe3b7d628dba65931e24b6c6704d3a1af69616341937765b6b60ba107ef46b0 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5449 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 5405 0.0 0.0 108700 924 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/e5a5abd22c3c43e31ef338a0107b5a04d7af02ccc998eb5510ded11d6161d2cb -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5430 0.0 0.0 42888 1000 ? Ss 05:33 0:00 | | \_ nginx: master process nginx -g daemon off;
nobody 5503 0.0 0.0 43340 1140 ? S 05:33 0:00 | | | \_ nginx: worker process
root 15448 0.0 0.0 18228 568 pts/0 Ss+ 06:15 0:00 | | \_ /bin/bash
root 5455 0.0 0.0 108700 840 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/8e7ebb37dd616576a1abe373e2abdd3b8440fed45f43ab9ec6657c5d56ded215 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5495 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 5466 0.0 0.0 108700 708 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/26a26134e8017ab0b11afbe4c63ee56abcd39f9da2a520c9ad84b90298e8dabc -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5512 0.0 0.0 964 4 ? Ss 05:33 0:00 | | \_ /pause
root 5689 0.0 0.0 108700 760 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/0f8198266867b08aa564f1df7c4944d69aa353d8c9b3df774d7313e3233c19ae -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 5750 0.2 0.6 747400 14084 ? SLsl 05:33 1:16 | | \_ /coredns -conf /etc/coredns/Corefile
root 5690 0.0 0.0 108700 608 ? Sl 05:33 0:01 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/35dbf007478374a58a84f3fb3c72b0b5204b7139f93db595cea857abb5cc6d36 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
user 5763 0.0 0.1 400484 3412 ? Ssl 05:33 0:03 | | \_ /metrics-sidecar
root 5694 0.0 0.0 110108 580 ? Sl 05:33 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/1b9adff49d51f82b32795182b80136ec3263e0ecb9f92cd3f20f58590c9521c5 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
user 5752 0.0 0.7 738016 15608 ? SLsl 05:33 0:11 | | \_ /dashboard --insecure-bind-address=0.0.0.0 --bind-address=0.0.0.0 --namespace=kubernetes-dashboard --enable-skip-login --disable-settings-authorizer
root 28475 0.0 0.0 110108 644 ? Sl 07:18 0:00 | \_ containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/00a54ebff34a65609c63f7b02d6deb64de8e8333cd42142709e7c1712700d6e1 -address /var/run/docker/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
root 28503 0.1 0.7 733960 14492 ? Ssl 07:18 0:33 | \_ /storage-provisioner
root 2956 0.0 0.0 12160 1132 ? Ss 05:33 0:00 \_ sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
root 3012 0.0 0.0 12020 500 ? Ss 05:33 0:00 \_ /usr/sbin/xinetd -pidfile /run/xinetd.pid -stayalive -inetd_compat -inetd_ipv6
root 3626 3.3 3.0 1932300 62468 ? Ssl 05:33 20:22 \_ /var/lib/minikube/binaries/v1.19.2/kubelet --bootstrap-kubeconfig=/etc/kubernetes/bootstrap-kubelet.conf --config=/var/lib/kubelet/config.yaml --container-runtime=docker --hostname-override=minikube --kubeconfig=/etc/kubernetes/kubelet.conf --node-ip=192.168.49.2
I don’t think its misleading.
What is a container? There is no such thing in Linux. Its just a process running in restricted namespaces (pid, mnt, net, etc…) so it appears isolated. And we call that abstraction a container.
What is a pod? Again I don’t think there is such a thing at the OS level, its just some containers sharing some namespaces. It is the Kubernetes abstraction of one or more containers running together which share some namespaces.
Kind regards,
czezz
October 30, 2020, 3:29pm
16
I just learnt that my statement about NS inside of Docker is not necessarily true.